In the latest Visual Studio Code release, you will find a range of GitHub Copilot features designed to make your coding and debugging experience in VS Code more productive and efficient. These features are now available for you to try out in the latest version of VS Code.
Vision (public preview)
You can now attach images and work with them directly in Copilot Chat. Share screenshots of errors and Copilot will interpret the image and resolve the issue. Or share mockups of new designs, and Vision will help you bring them to life.
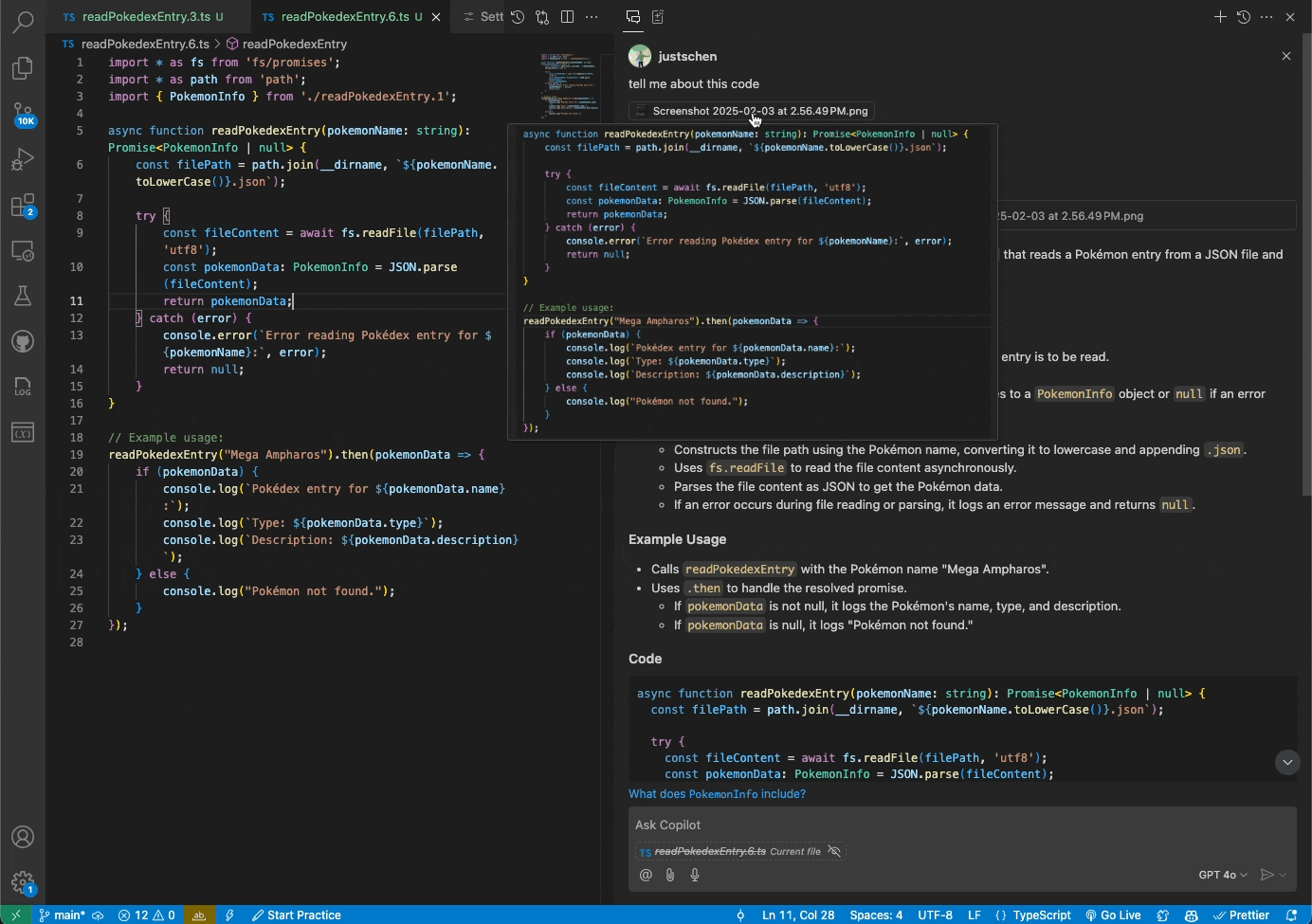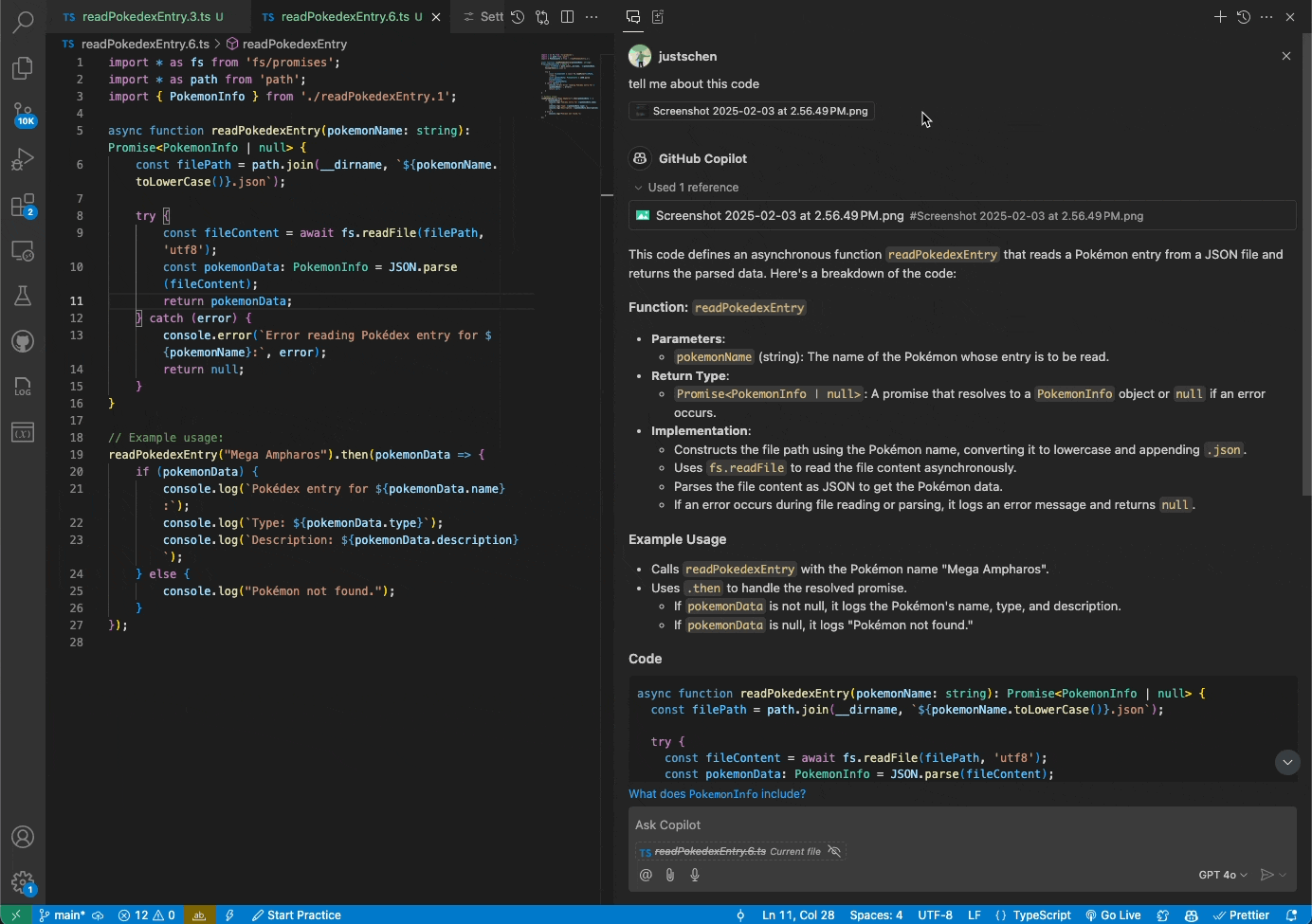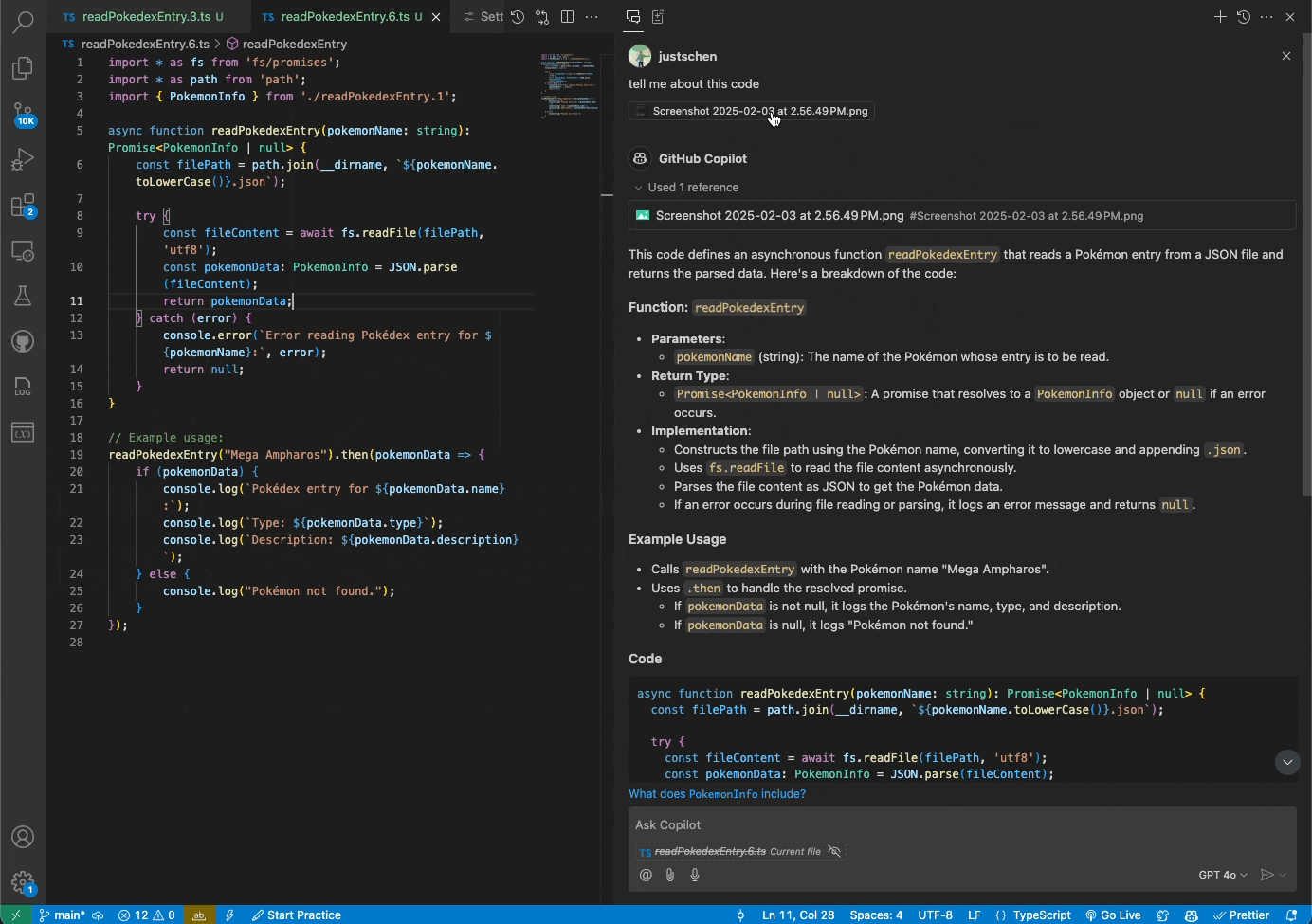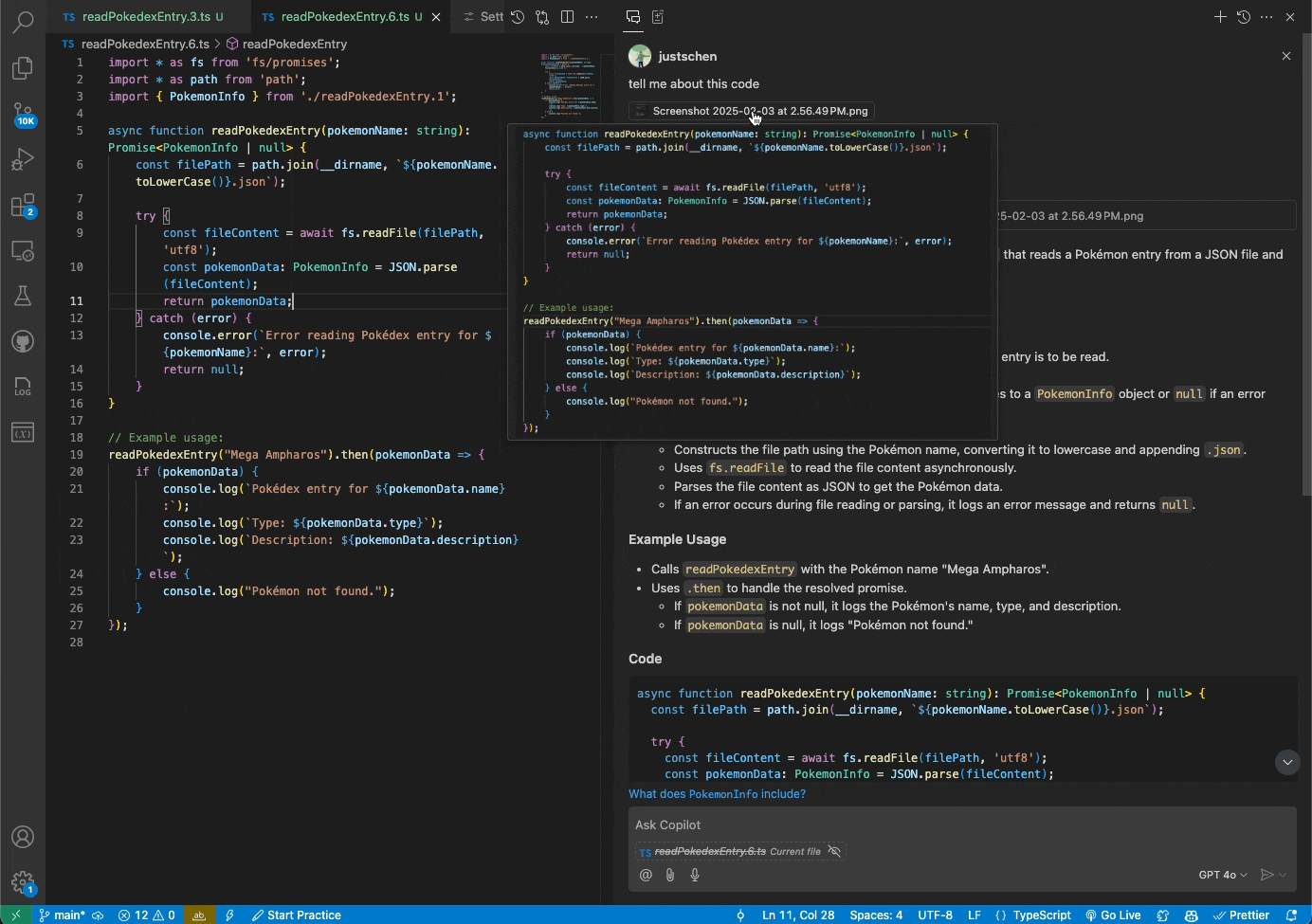
Getting started
Vision is available today in the VS Code Insiders release. You can drag and drop images into Chat, paste them from a clipboard, or attach them through the VS Code UI. Vision requires that you use the GPT-4o model and upload one of the following file types: JPEG/JPG, PNG, GIF, and WEBP.
Agent mode (public preview)
As of today’s VS Code Insiders release, a new agent mode is available for GitHub Copilot Edits. You can opt in to this experience via the VS Code setting github.copilot.chat.agent.enabled.
In agent mode, Copilot can iterate on its own code. This includes automatically identifying and fixing errors, executing terminal commands to complete a requested task, and resolving runtime errors with self-healing capabilities. GitHub Copilot can now infer the other tasks that were not specified and also need to be completed in order for your explicit request to work.

Agent mode will continue to improve over the coming weeks. Please share your feedback as you try it out (today in VS Code Insiders, and soon in Stable).
Next edit suggestions (public preview)
Next edit suggestions use recent edits that you’ve made to anticipate the next edit you might want to make, and where that edit is located.
With this new ability, GitHub Copilot will suggest revisions to your code, comments, tests, and more. Next edit suggestions help you edit code that you (or others) have previously written and need to edit to better meet your current goals.
Getting started
You can enable next edit suggestions via the VS Code setting github.copilot.nextEditSuggestions.enabled. If you are a Copilot Business or Enterprise user, you will also need your Administrator to enable next edit suggestions for your organization by opting in to Copilot “Editor Preview Features”.
Using next edit suggestions
When you’re presented with an edit suggestion, you can navigate to it with the Tab key and then accept it with the Tab key again, saving you time to find the next relevant edit (no manual searching through files or references required). An arrow in the gutter indicates whether an edit suggestion is available.
In the example below, next edit suggestions help with a challenging mistake in logic.

For more scenarios where next edit suggestions will help, visit the Visual Studio Code docs.
Prompt files (public preview)
Prompt files allow you and your team to build, store, and share reusable prompts. They contain pre-defined instructions and context for GitHub Copilot Chat and Copilot Edits, which will help you save time, maintain consistency, and support the sharing of best practices across workflows for shared development tasks and domains.
They complement custom instructions through their flexibility for specific tasks and scalability for complex projects with multiple workflows.
Getting started
To enable prompt files, set the VS Code setting chat.promptFiles to true.
Copilot Edits (GA)
With Copilot Edits, you can smoothly make changes to one or more of your files directly from Copilot Chat. This feature, which has been in preview since the October VS Code release, is now generally available.
To learn more about Copilot Edits, visit the VS Code docs.

