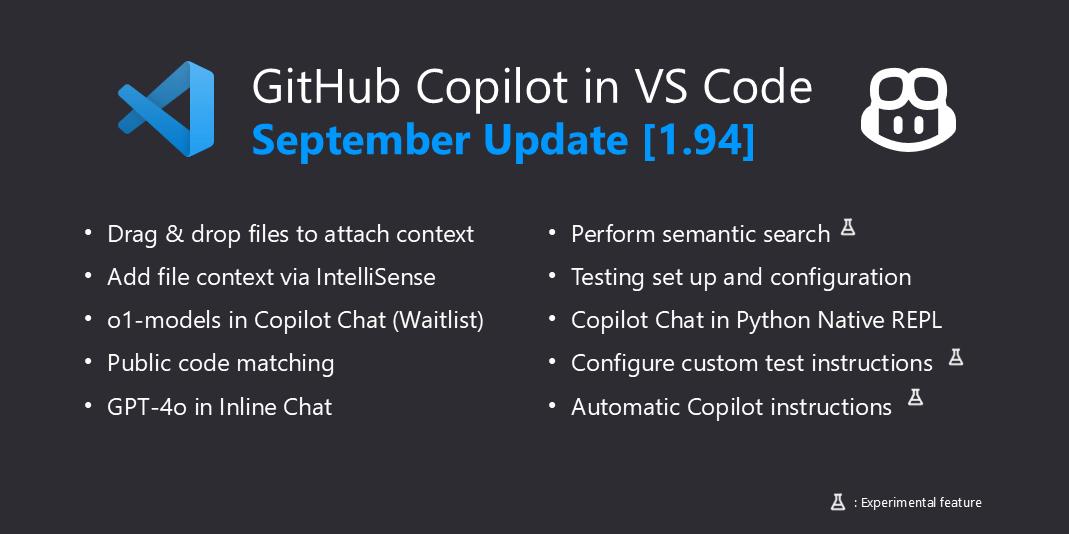
In the latest Visual Studio Code release, you will find a suite of enhancements to GitHub Copilot Chat, designed to streamline your coding, debugging, and testing processes.
These features are now available for you to try out in the latest version of Visual Studio Code.
Pick your language model
Sign up for early access to the latest OpenAI o1 models for more precise and efficient coding assistance. Once you have access, you will have the model picker control in Copilot Chat in VS Code. You can then choose which model version to use for your chat conversations.
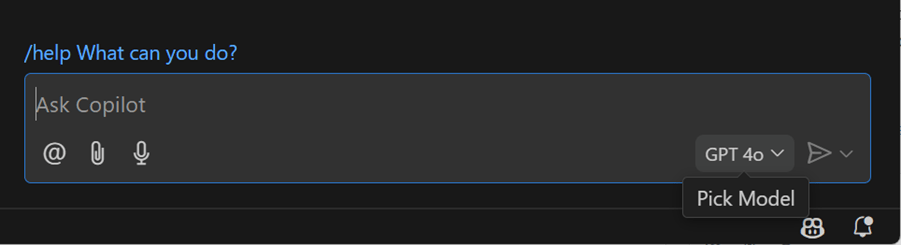
Enhanced code quality with GPT-4o
Copilot Inline Chat now uses GPT-4o, giving you faster, more accurate, and higher-quality code and explanations when you use Chat in the editor.
Public code matching in chat
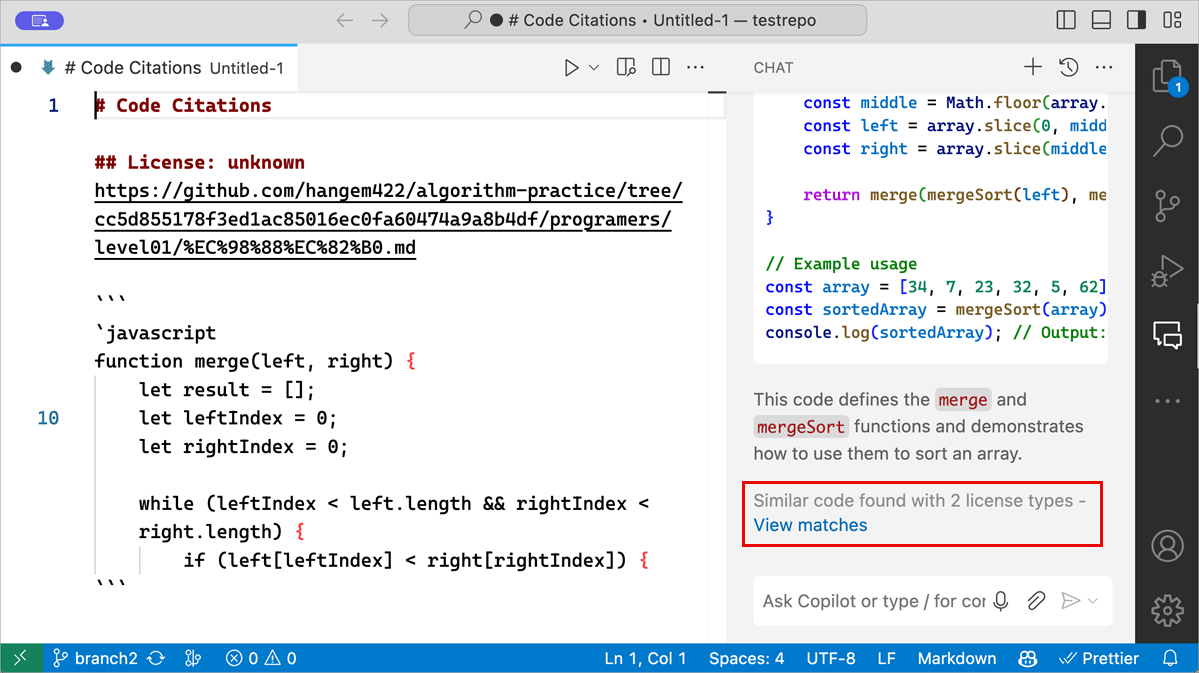
You can allow GitHub Copilot to return code that could match publicly available code on GitHub.com. When this functionality is enabled for your organization subscription or personal subscription, Copilot code completions already provided you with details about the matches that were detected. We now show you these matches for public code in Copilot Chat as well.
If this is enabled for your organization or subscription, you might see a message at the end of the response with a View matches link. If you select the link, an editor opens that shows you the details of the matching code references with more details.
File suggestions in chat
In chat input fields, you can now type # to get file name suggestions and quickly attach them to your prompt as context. This works in chat locations that support file attachments, such as the Chat view, Quick Chat, Inline Chat, and Notebook Chat.
Drag and drop files to add chat context
You can now attach additional files as context for a chat prompt by dragging files or editor tabs from the workbench directly into chat. For Inline Chat, hold Shift and drop a file to add it as context instead of opening it in the editor.
File attachments included in history
When you attach a file or editor selection as relevant context to your chat request, Copilot Chat will include them in the history of follow-on requests so that you can keep referring to them without having to reattach them. Previously, this context was added only for the current request and was not included in the history of follow-on requests.

Inline Chat and completions in Python native REPL
The native REPL editor, used by the Python extension, now supports Copilot Inline Chat and code completions directly in the input box.
Semantic search results (Preview)
Setting: github.copilot.chat.search.semanticTextResults
You can perform an exact search across your files with the Search view. It also now uses Copilot to give search results that are semantically relevant.
This functionality is still in preview and by default, the setting is not enabled. Try it out and let us know what you think!
Fix test failure (Preview)
Setting: github.copilot.chat.fixTestFailure.enabled
New fix test logic now helps you diagnose failing unit tests. This logic is triggered in some scenarios by the /fix slash command, and you can also invoke it directly with the /fixTestFailure slash command. The command is enabled in chat by default but can be disabled via the setting github.copilot.chat.fixTestFailure.enabled.
Automated test setup (Experimental)
Setting: github.copilot.chat.experimental.setupTests.enabled
You can now use an experimental /setupTests slash command to configure the testing set up for your workspace. This command can recommend a testing framework, provide steps to set up and configure it, and suggest a VS Code extension to provide testing integration in VS Code.
When you use the /tests command to generate tests for your code, Copilot Chat can recommend /setupTests and testing extensions if it looks like such an integration has not been set up yet in your workspace.
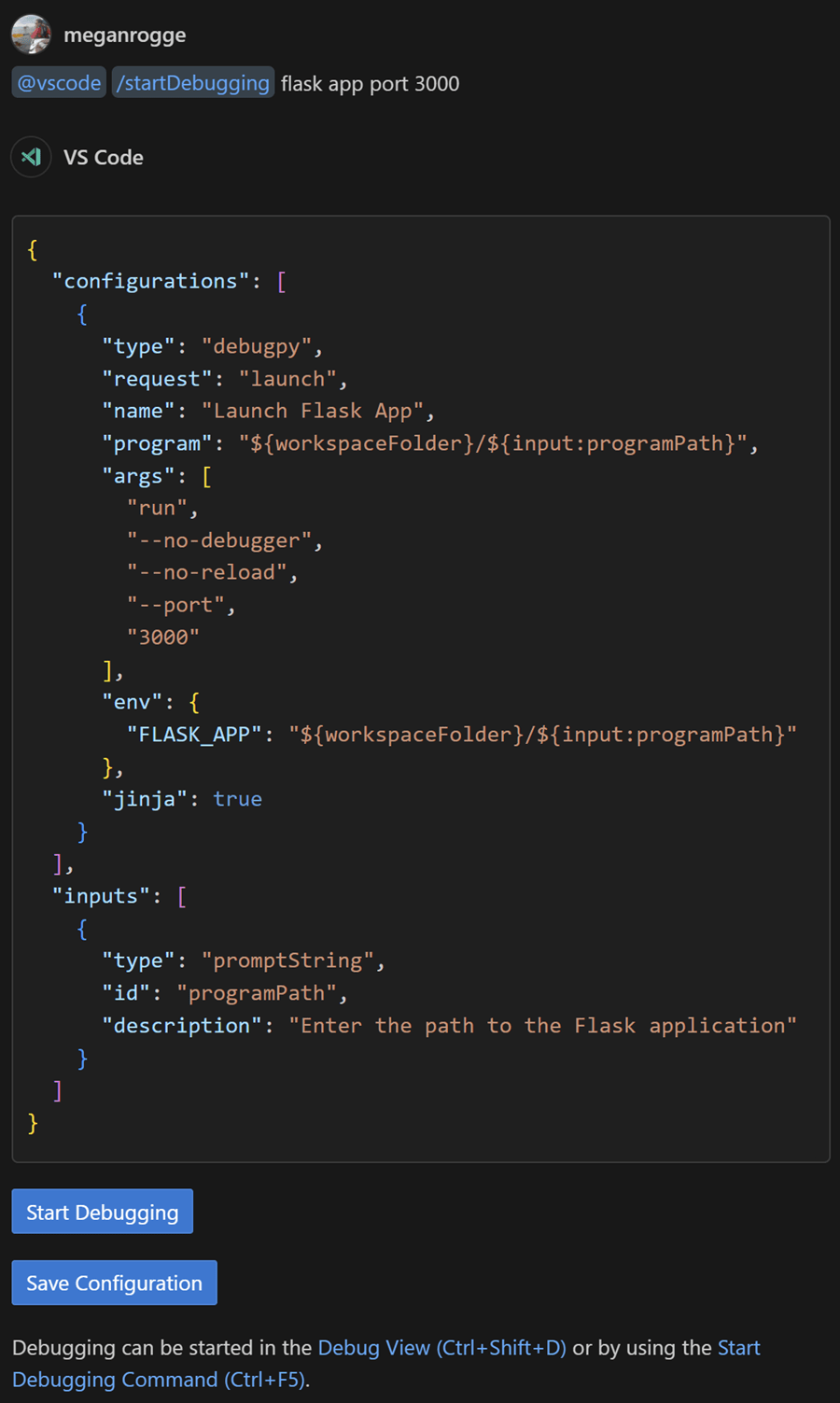
Start debugging from Chat (Experimental)
Setting: github.copilot.chat.experimental.startDebugging.enabled
You can use the /startDebugging slash command to find or create a launch configuration and start debugging your application. When you use @vscode in Copilot Chat, /startDebugging is now available by default.
Chat in Command Center (Experimental)
Setting: chat.commandCenter.enabled
You can now access chat via the Command Center, which provides access to all relevant chat commands, like starting the different chat experiences or attaching context to your prompt. Note that the Command Center itself needs to be enabled for the chat Command Center entry to show.
Custom test generation instructions (Experimental)
Generating tests with Copilot helps you write code that is more robust. With custom instructions you can ensure that the generated tests meet your specific coding style and requirements.
Setting: github.copilot.chat.experimental.testGeneration.instructions
In addition, you can now define instructions for test generation in settings or import them from a file. For example, if you always want to use a particular unit testing framework for your tests. Configure the test-generation instructions in the github.copilot.chat.experimental.testGeneration.instructions setting.
✍️ We want your feedback
Try out these new features and share your experiences and feedback in our issues.

