Advance File Permissions in Linux
Last Updated :
03 Jul, 2020
The Linux file permissions are not limited to “rwx” bits, there are 3 special permissions apart from these “rwx” permissions which are SUID,SGID,The Sticky Bit. This article is about the 3 special file permissions and how to set and remove those permission bits.
Set-user-ID (SUID)
In Linux by default when a user executes a file, The file gets executed with the privileges of the user who executes it. If we set SUID(set-user-ID) bit on the executable this behavior can be changed, then the file will always run with privileges of the owner of the file, no matter who runs the executable.
Note: Only owner of the file or root can set the SUID bit
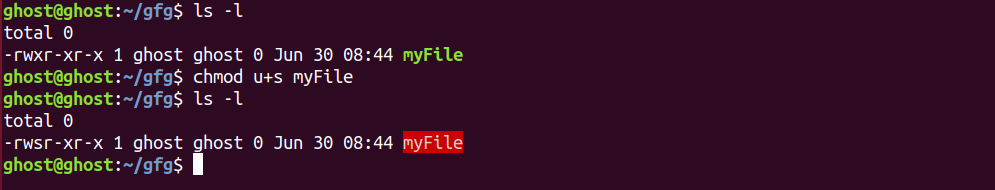
1. You can set SUID bit by passing u + s to the chmod command:
2. Alternatively, you can use octal notional by prefixing “4” to the octal string. (like 4724 instead of 724).
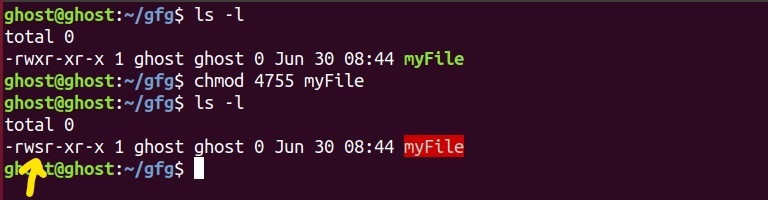
As you notice “s” letter instead of usual “x” to execute permission for the owner. This letter “s” indicates that SUID(set-user-ID) bit has been set for the file or directory in question.
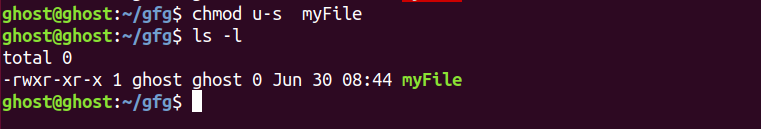
3. You can remove SUID bit by passing u – s to the chmod command:
Set-group-ID (SGID)
Set-group-ID bit on a file: Set-group-ID (SGID) is similar to SUID except that, an executable with SGID bit set runs with the privileges of the group which owns of the file
1. You can set SGID bit by passing g + s to the chmod command:
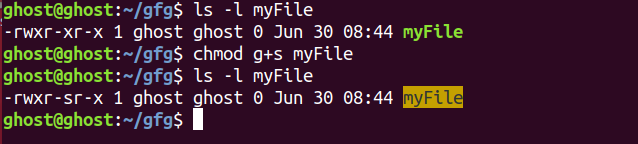
2. Alternatively, you can use octal notional by prefixing “2” to the octal string. (like 2755 instead of 755).
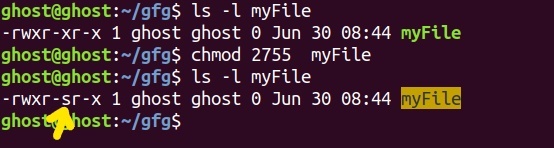
As you notice “s” letter instead of usual “x” in execute permission for the group. This letter “s” indicates that SGID(set-group-ID) bit has been set for the file or directory in question.
3. You can remove SGID bit by passing g – s to the chmod command:
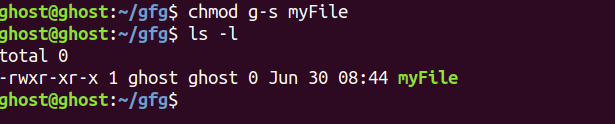
Set-group-ID bit on a directory: When set-group-ID (SGID) bit is set directory, all newly created subdirectories/files under the directory will inherit the same group ownership as of the directory itself. If the SGID bit is not set then all newly created files will have a group as the user’s default group.
Set-group-ID is very useful in multi-user setup where users with different primary group have access each others files as shown in this article.
Here is an example to better understand this.
1.Let’s create a directory parent which is owned by user: root and group: root.
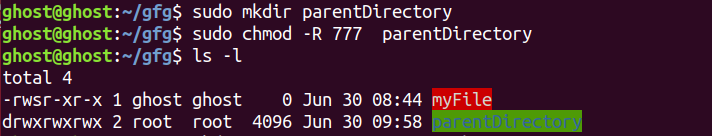
2.Now if we create a sub-directory under parent from the different user then that directory will have group-owner default to the user’s primary group.
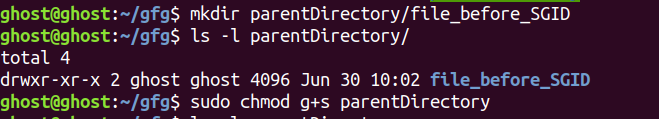
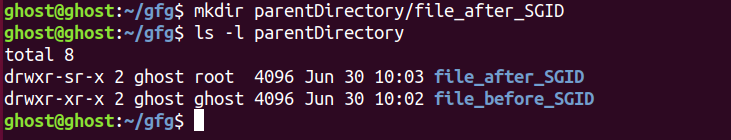
3.Now if we set SGID bit for parent and again create new sub-directory under parent then this time it will have group default to parent’s group. This is because the parent had the SGID bit set, and the newly created subdirectories/files under it will inherit the parent‘s group.
The Sticky Bit
If the sticky bit on a directory is set, subdirectories/Files under that directory can only be deleted by either owner of the file, owner of the directory, or the root user. This special permission is useful to prevent users from deleting other user’s file inside a shared folder where everyone has read, write, and execute access.
Let see an example.
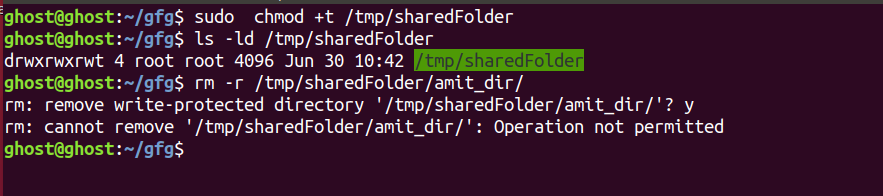
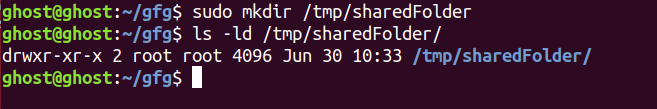
1.Let start by creating a shared folder where everyone has read, write, and execute permission.
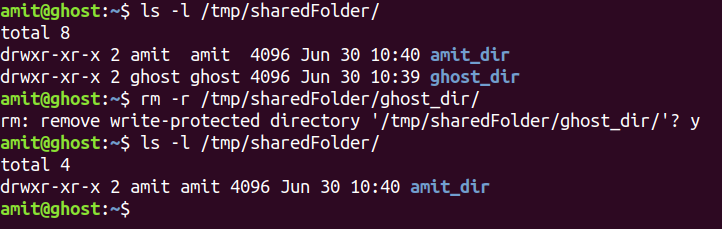
2.Inside this shared folder, it is possible to remove directory/files of other users.
3.Now let’s set the sticky bit on the sharedFolder.
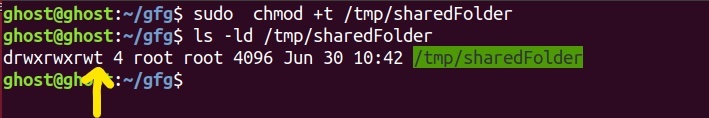
As you notice “t” letter instead of usual “x” in execute permission for the others. This letter “t” indicates that a sticky bit has been set for the file or directory in question. Now because the sticky bit is set on the sharedFolder, files/directory could only be deleted by the owners or root user.